Microsoft today released updates to plug at least 121 security holes in its Windows operating systems and software, including one vulnerability that is already being exploited in the wild. Eleven of those flaws earned Microsoft’s most-dire “critical” rating, meaning malware or malcontents could exploit them with little to no interaction from Windows users. The zero-day […]
Cyber agencies urge organizations to collaborate to stop fast flux DNS attacks
It’s “a defensive gap in many networks,” the report says. The agencies recommend that all stakeholders, both government and providers, collaborate on developing and implementing scalable solutions to close this gap. However, the report admits, differentiating fast flux from legitimate activity “remains an ongoing challenge.” For example, some common content delivery network (CDN) behaviors may […]
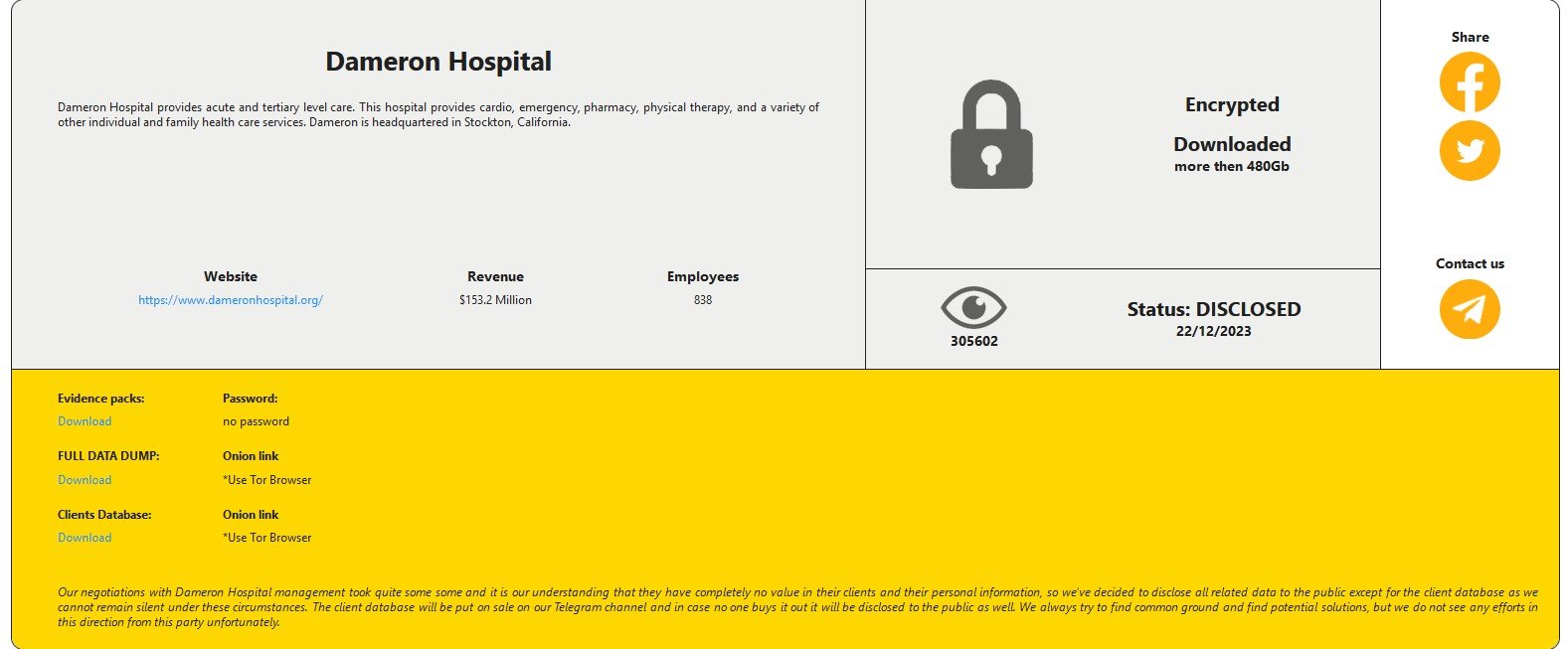
16 months after they experienced a ransomware attack, Dameron Hospital notifies those affected – DataBreaches.Net
In 2017, Dameron Hospital in Texas reported a breach to the California Attorney General’s Office. No copy of its breach notification was uploaded to California’s breach site, and Dameron did not respond to this site’s email asking for details of the breach. The incident never appeared on HHS’s public breach tool, so we never found […]
Secure Ideas Achieves CREST Accreditation and CMMC Level 1 Compliance
Jacksonville, United States, April 3rd, 2025, CyberNewsWire Secure Ideas, a premier provider of penetration testing and security consulting services, proudly announces its recent achievements of CREST accreditation and CMMC Level 1 compliance, reinforcing its commitment to delivering the highest standards of security assessment and regulatory compliance for its clients. With these certifications, Secure Ideas strengthens […]
Best 10 Patch My PC Alternatives and Competitors
Keeping Windows applications up to date is a challenge, and Patch My PC seems to be a favorite for automating the process. Some of its users praise the solution’s lightweight agent and strong third-party app support. However, this tool also has its downsides: a reviewer on G2 says that only one user can be in […]
Apache Tomcat: CVE-2025-24813: Active Exploitation
What is CVE-2025-24813? CVE-2025-24813 is a critical path equivalence vulnerability in Apache Tomcat, with exploitation attempts by threat actors observed in the wild. The vulnerability allows attackers to execute arbitrary code on vulnerable servers without authentication under specific conditions, potentially leading to system compromise and sensitive data being exposed. Organizations affected by the configuration required […]
Microsoft warns of critical flaw in Canon printer drivers
Microsoft warns of critical flaw in Canon printer drivers Pierluigi Paganini April 01, 2025 Microsoft’s offensive security team discovered a critical code execution vulnerability impacting Canon printer drivers. Researchers at Microsoft’s Offensive Research and Security Engineering (MORSE) team have discovered a critical code execution vulnerability, tracked as CVE-2025-1268 (CVSS score of 9.4), impacting Canon printer […]
How Will the Splinternet Impact Cybersecurity
Most people think of the internet as a globally connected resource. However, user experiences are not necessarily as consistent as they believe. Factors such as politics, regulations and censorship have made the internet a fragmented “splinternet” for some users. What are the potential implications for cybersecurity? Changes in Social Media Platforms’ Policies In the early […]
Twitter (X) Hit by 2.8 Billion Profile Data Leak in Alleged Insider Job
Massive Twitter (X) profile data leak exposes details of 2.8 billion users; alleged insider leak surfaces with no official response from the company. A data leak involving a whopping 2.87 billion Twitter (X) users has surfaced on the infamous Breach Forums. According to a post by a user named ThinkingOne, the leak is the result […]
Top 5 Web Application Penetration Testing Companies UK
Web Application Penetration Testing (WAPT) is a methodical approach to security that involves ethical hackers simulating real-world cyber-attacks on your web application to uncover vulnerabilities. By mimicking the tactics of cybercriminals, these professionals can identify weaknesses before malicious actors can exploit them. This proactive process allows businesses to address security flaws early and maintain a […]