Cary, North Carolina, March 13th, 2025, CyberNewsWire As Artificial Intelligence (AI)-powered cyber threats surge, INE Security, a global leader in cybersecurity training and certification, is launching a new initiative to help organizations rethink cybersecurity training and workforce development. The company warns that AI is reshaping both the threat landscape and the skills required for cybersecurity […]
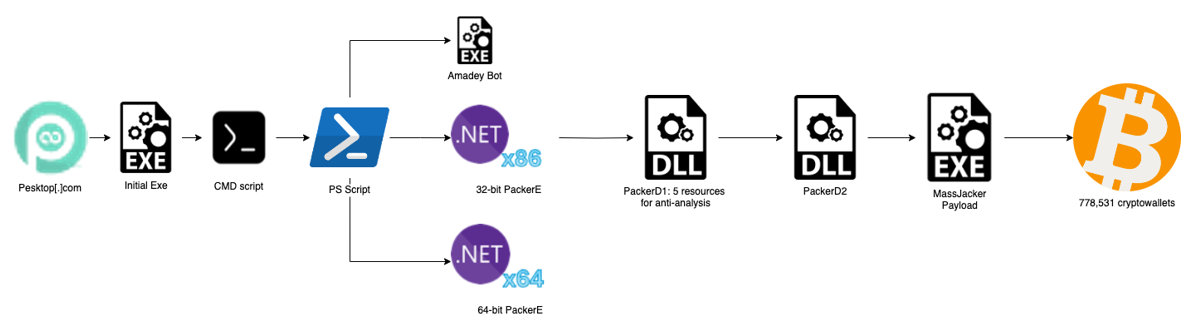
New MassJacker clipper targets pirated software seekers
New MassJacker clipper targets pirated software seekers Pierluigi Paganini March 15, 2025 Pirated software seekers are targeted by the new MassJacker clipper malware, according to CyberArk researchers. A new malware campaign spreading a new clipper malware dubbed MassJacker targets users searching for pirated software, Cyberark users warn. A clipper malware is a type of malicious […]
Best Practices to Prevent Theft and Fraud
Cybersecurity tips to protect your cryptocurrency from hackers, scams, and fraud. Learn best practices for securing digital assets and staying safe online. The cryptocurrency market is changing and growing daily, with new coins created weekly. While the broader market is struggling with weak demand and remains at a critical juncture, Cardano’s ADA is among the […]
2024 Malicious Infrastructure Insights: Key Trends and Threats
Executive Summary In 2024, Insikt Group significantly expanded its tracking of malicious infrastructure by covering more malware families and categories, additional infrastructure types such as staging servers, and integrating data sources like Recorded Future® Network Intelligence, enhancing threat detection, higher-tier infrastructure insights, and victimology analysis. While many key 2023 trends persisted — such as Cobalt […]
Cold Wallets vs. Hot Wallets: Which Offers Better Security?
Cryptocurrency isn’t just a buzzword anymore. By December 2024, the number of global cryptocurrency owners reached approximately 659 million, marking a 13% increase from January 2024. That might not sound like a massive chunk, but it still represents millions of individuals who want to protect their virtual holdings. Where regular banking once ruled, self-managed wallets […]
Chromecast chaos – 2nd gen devices go belly-up as Google struggles to fix certificate issue
Has your old Chromecast suddenly developed a problem? You’re not alone it seems. Many users of second-generation Chromecast and Chromecast Audio streaming devices have discovered that their beloved dongles have gone belly-up and are showing error messages such as: “Untrusted device: [name] couldn’t be verified. This could be caused by outdated firmware.” And what has […]
Federal Judges Block Trump’s Mass Firings of Federal Workers
Government , Industry Specific Restraining Order Allows Dismissed Cyber Defense Agency Employees to Return to Work Chris Riotta (@chrisriotta) • March 14, 2025 Image: Shutterstock A U.S. federal judge temporarily blocked a Trump administration effort to fire thousands of federal employees including at the Department of Homeland Security, where the U.S. cyber defense […]
Quantifying cyber risk strategies to resonate with CFOs and boards
In this Help Net Security interview, Mir Kashifuddin, Data Risk & Privacy Leader at PwC, discusses how CISOs can translate cyber risk into business value and secure a more strategic role within their organizations. He explains that aligning cybersecurity with business objectives and leveraging data governance, AI, and financial risk quantification drives resilience and growth. […]
New Akira ransomware decryptor cracks encryptions keys using GPUs
Security researcher Yohanes Nugroho has released a decryptor for the Linux variant of Akira ransomware, which utilizes GPU power to retrieve the decryption key and unlock files for free. Nugroho developed the decryptor after being asked for help from a friend, deeming the encrypted system solvable within a week, based on how Akira generates encryption […]
Quantifying cyber risk strategies to resonate with CFOs and boards
In this Help Net Security interview, Mir Kashifuddin, Data Risk & Privacy Leader at PwC, discusses how CISOs can translate cyber risk into business value and secure a more strategic role within their organizations. He explains that aligning cybersecurity with business objectives and leveraging data governance, AI, and financial risk quantification drives resilience and growth. […]