In 2024, we introduced Generative AI features in the Sophos Extended Detection and Response (XDR) platform, empowering security analysts to operate confidently and make smart decisions fast. Today, we are excited to extend these capabilities with the launch of the Sophos AI Assistant. Crafted by experts, created for everyone Designed and developed by Sophos experts […]
How Phished Data Turns into Apple & Google Wallets – Krebs on Security
Carding — the underground business of stealing, selling and swiping stolen payment card data — has long been the dominion of Russia-based hackers. Happily, the broad deployment of more secure chip-based payment cards in the United States has weakened the carding market. But a flurry of innovation from cybercrime groups in China is breathing new […]
CIOs and CISOs take on NIS2: Key challenges, security opportunities
Antolini himself highlights that AMA’s cybersecurity budget had to increase due to the adjustment to the NIS2 requirements. “We had to make a lot of investments, for example to strengthen the systems and to have the right number of people to manage them and follow the procedures”, says AMA’s CISO. “NIS2, in fact, requires reporting […]
CIOs and CISOs take on NIS2: Key challenges, security opportunities
Antolini himself highlights that AMA’s cybersecurity budget had to increase due to the adjustment to the NIS2 requirements. “We had to make a lot of investments, for example to strengthen the systems and to have the right number of people to manage them and follow the procedures”, says AMA’s CISO. “NIS2, in fact, requires reporting […]
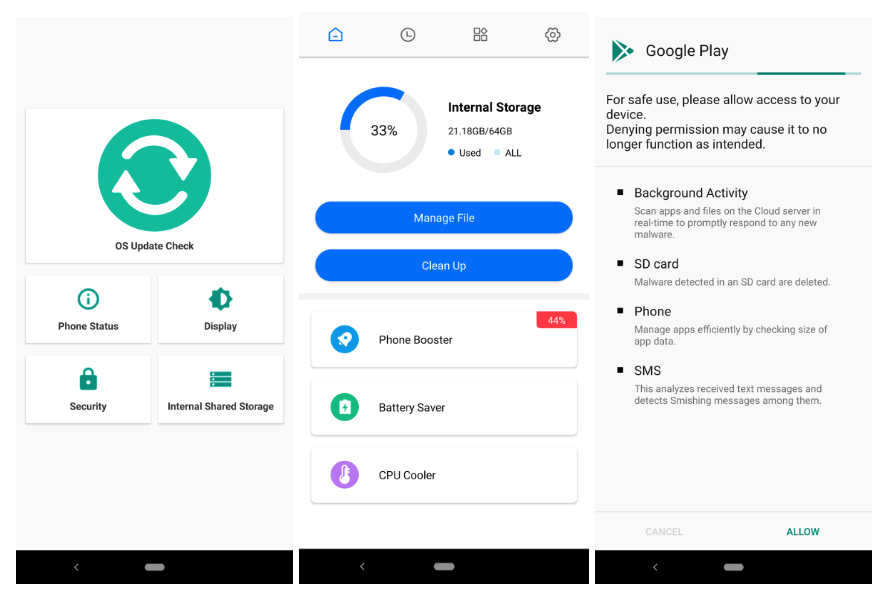
North Korea-linked APT group ScarCruft spotted using new Android spyware KoSpy
North Korea-linked APT group ScarCruft spotted using new Android spyware KoSpy Pierluigi Paganini March 13, 2025 North Korea-linked APT group ScarCruft used a new Android spyware dubbed KoSpy to target Korean and English-speaking users. North Korea-linked threat actor ScarCruft (aka APT37, Reaper, and Group123) is behind a previously undetected Android surveillance tool named KoSpy that was used to […]
8 Essential Steps for DORA Compliance and Effective Reporting
In 2024, every major European financial service (FS) firm suffered some kind of security breach. These shocking findings come from a study of cyber incidents in Europe last year. It found that 18% of large FS companies suffered direct breaches (where hackers broke into their systems). The rest were exposed through third- or fourth-party breaches […]
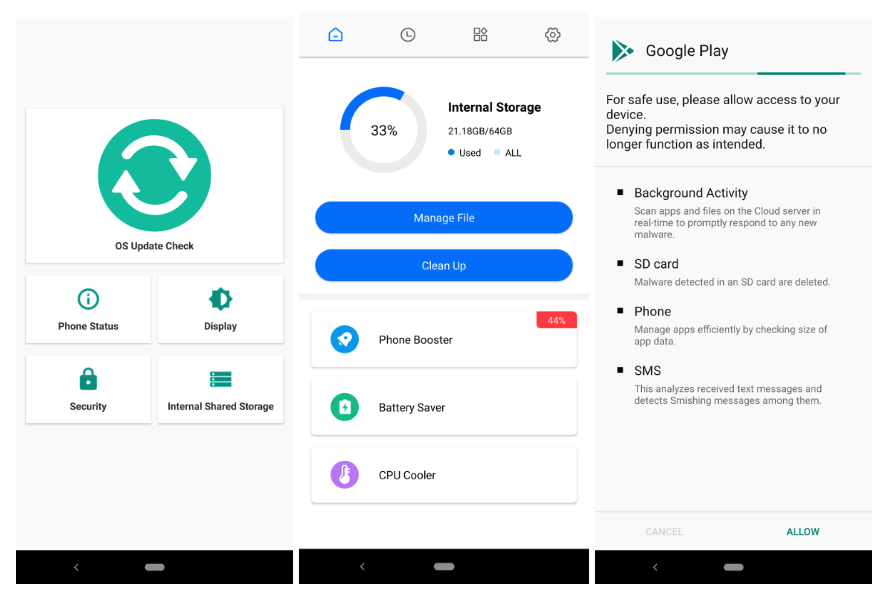
North Korea-linked APT group ScarCruft spotted using new Android spyware KoSpy
North Korea-linked APT group ScarCruft spotted using new Android spyware KoSpy Pierluigi Paganini March 13, 2025 North Korea-linked APT group ScarCruft used a new Android spyware dubbed KoSpy to target Korean and English-speaking users. North Korea-linked threat actor ScarCruft (aka APT37, Reaper, and Group123) is behind a previously undetected Android surveillance tool named KoSpy that was used to […]
North Korea-linked APT group ScarCruft spotted using new Android spyware KoSpy
North Korea-linked APT group ScarCruft spotted using new Android spyware KoSpy Pierluigi Paganini March 13, 2025 North Korea-linked APT group ScarCruft used a new Android spyware dubbed KoSpy to target Korean and English-speaking users. North Korea-linked threat actor ScarCruft (aka APT37, Reaper, and Group123) is behind a previously undetected Android surveillance tool named KoSpy that was used to […]
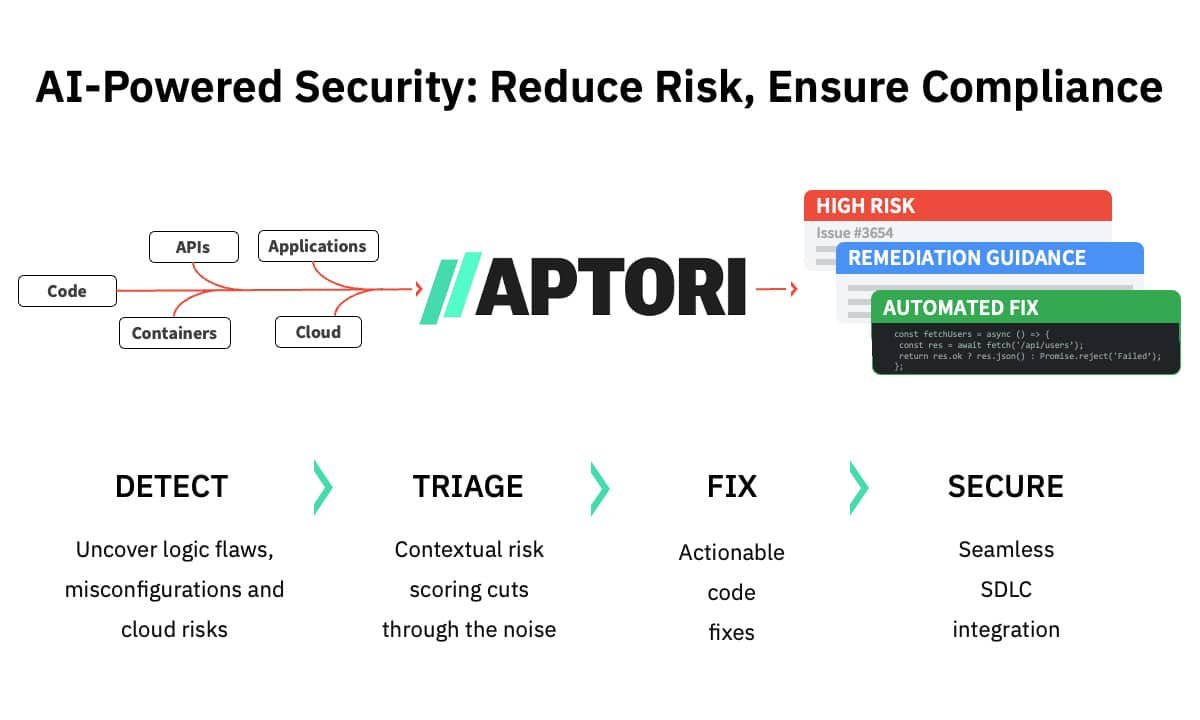
Aptori Now on Google Cloud Marketplace for AI-Powered Security and Automated Risk Remediation
San Jose, United States / California, March 12th, 2025, CyberNewsWire Aptori’s AI-Driven AppSec Platform Proactively Eliminates Vulnerabilities to Minimize Risk and Ensure Compliance. Aptori, a leader in AI-driven application security, today announced the launch of its AI-driven AppSec Platform on Google Cloud Marketplace as part of graduating from Google Cloud’s ISV Startup Springboard program. This […]
RedMike Exploits Unpatched Cisco Devices in Global Telecommunications Campaign
Executive Summary Between December 2024 and January 2025, Recorded Future’s Insikt Group identified a campaign exploiting unpatched internet-facing Cisco network devices primarily associated with global telecommunications providers. Victim organizations included a United States-based affiliate of a United Kingdom-based telecommunications provider and a South African telecommunications provider. Insikt Group attributes this activity to the Chinese state-sponsored […]