Microsoft patched 57 vulnerabilities affecting its foundational systems and core products, including six actively exploited zero-day vulnerabilities, the company said in its latest security update Tuesday. Four of the six zero-days, which were all added to the Cybersecurity and Infrastructure Security Agency’s known exploited vulnerabilities catalog, are high-severity on the CVSS scale. The software defects […]
Category: Uncategorized
Deserialized web security roundup: Twitter 2FA backlash, GoDaddy suffers years-long attack campaign, and XSS Hunter adds e2e encryption
Your fortnightly rundown of AppSec vulnerabilities, new hacking techniques, and other cybersecurity news Twitter faced further criticism this week when Elon Musk’s social networking platform announced SMS-based 2FA will only be available to paying customers going forward. The social media site historically enabled two-factor authentication (2FA) to all users, providing they connected their mobile phone […]
Trump’s Spy Chief Urged to Declassify Details of Secret Surveillance Program
Senator Ron Wyden of Oregon, a renowned privacy hawk who has served on the Senate intelligence committee since just after 9/11, has referred to the new provision as “one of the most dramatic and terrifying expansions of government surveillance authority in history.” Declassifying the new types of businesses that can actually be considered an ECSP […]
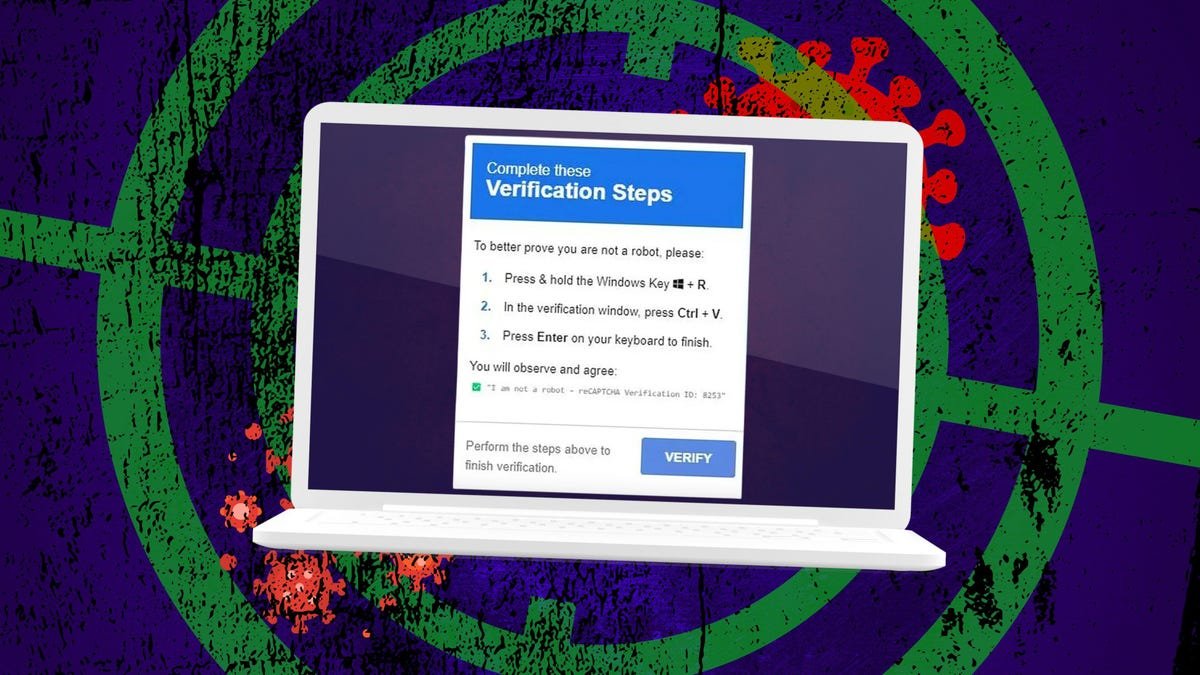
That weird CAPTCHA could be a malware trap – here’s how to protect yourself
ZDNET A persistent malware campaign is exploiting the ubiquitous CAPTCHA process to try to steal data from unsuspecting victims. Also: Got a suspicious E-ZPass text? It’s a trap – how to spot the scam As described by security firm Malwarebytes in a new report, this scheme relies on the ease with which people often follow the […]
Generative AI red teaming: Tips and techniques for putting LLMs to the test
OWASP recommends evaluating generative AI systems in phases, including models, implementation, systems, and runtime, as seen below: OWASP Each of these phases has key considerations, such as the model’s provenance and data pipelines, testing guardrails that are in place for implementation, examining the deployed systems for exploitable components, and targeting runtime business processes for potential […]
Hiring privacy experts is tough — here’s why
The nature of privacy work also varies by country, which adds another layer of complexity. “The privacy space is largely underpinned by legislation, which varies from country to country. Cybersecurity, on the other hand, tends to revolve around technology, and as a result is more agnostic and universal,” Michael Trovato, managing partner at IIS and […]
Best Automated Patch Management Software in 2025
Did you know? — Recent research shows that 80% of cyberattacks happen due to unpatched software vulnerabilities. This highlights the critical role of automated patch management software in safeguarding systems. These tools not only streamline updates but also fortify your systems against evolving cyber threats. In this article, we’ll talk about the best automated patch […]
Bubba AI, Inc. is launching Comp AI to help 100,000 startups get SOC 2 compliant by 2032.
San Francisco, California, March 3rd, 2025, CyberNewsWire With the growing importance of security compliance for startups, more companies are seeking to achieve and maintain compliance with frameworks like SOC 2, ISO 27001 & GDPR. Bubba AI, Inc. is building a comprehensive solution for these organizations to easily integrate compliance workflows and build their own customized […]
Why AI-powered security tools are your secret weapon against tomorrow’s attacks
Yaroslav Kushta/Getty Images It’s an age-old adage of cyber defense that an attacker has to find just one weakness or exploit, but the defender has to defend against everything. The challenge of AI, when it comes to cybersecurity, is that it is an arms race in which weapons-grade AI capabilities are available to both attackers […]
Business Contingency Plans for 2025-2049
Executive Summary Businesses should now begin making preparatory investments to establish contingency plans in case of a Taiwan invasion, especially if they operate in Taiwan or China, rely heavily on supply chains or shipping in Asia, or are located in countries likely to oppose China’s geopolitical objectives. While an invasion in the short term (2025–2026) […]