Aptori’s AI-Driven AppSec Platform Proactively Eliminates Vulnerabilities to Minimize Risk and Ensure Compliance. Aptori, a leader in AI-driven application security, today announced the launch of its AI-driven AppSec Platform on Google Cloud Marketplace as part of graduating from Google Cloud’s ISV Startup Springboard program. This new agentic AI solution leverages semantic reasoning to analyze application […]
Category: Uncategorized
How to Prepare for NIS2 Audits
Third-party security questionnaires and the number of audits that are growing every year are killing everybody’s soul! – Larisa Mihai, Cyber Compliance Expert In October 2024, European Union member states had a deadline to transpose the NIS2 Directive into national law. Although not all countries have begun enforcing the rules, it will eventually become the […]
Cleo MFT Vulnerability CVE-2024-50623: Critical RCE Risk
What is CVE-2024-50623 CVE-2024-50623 is a critical unrestricted file upload and download vulnerability that could lead to remote code execution (RCE). What are the affected products? The vulnerability affects Cleo’s managed file transfer (MFT) products Harmony, VLTrader, and LexiCom before version 5.8.0.21. Cleo Harmony 5.8 Cleo LexiCom 5.5.0.0 Cleo LexiCom 5.6 Cleo LexiCom 5.6.1 Cleo […]
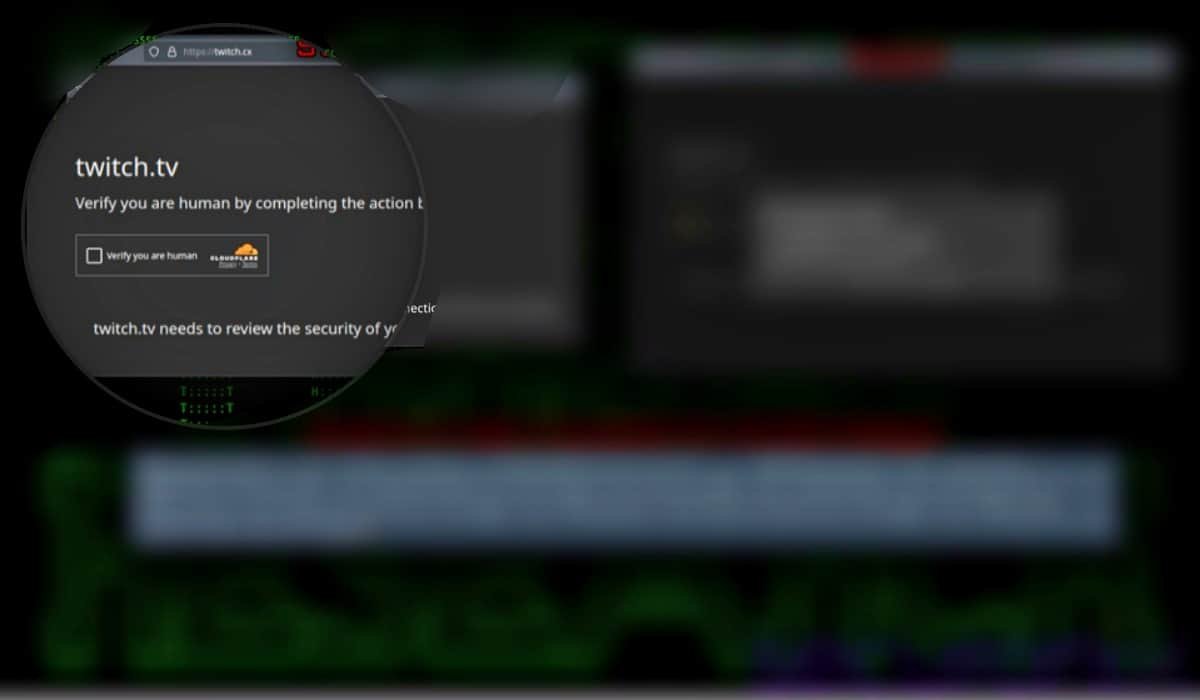
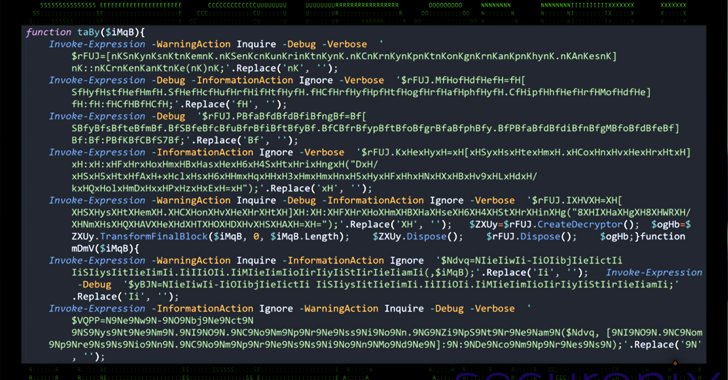
New OBSCURE#BAT Malware Targets Users with Fake Captchas
OBSCURE#BAT malware campaign exploits social engineering & fake software downloads to evade detection, steal data and persist on systems. Learn how to stay safe. Cybersecurity researchers at Securonix Threat Labs have spotted a new malware campaign called OBSCURE#BAT. This campaign uses social engineering tactics and fake software downloads to trick users into executing malicious code, […]
Fake police call cryptocurrency investors to steal their funds
Have you had a phone call from police about your cryptocurrency wallet? Be on your guard – you could be about to be scammed. That’s the clear warning issued by police in England, as it was disclosed how nine people have lost a combined £1 million in a phone-related cryptocurrency scam. According to the Kent […]
Microsoft apologizes for removing VSCode extensions used by millions
Microsoft has reinstated the ‘Material Theme – Free’ and ‘Material Theme Icons – Free’ extensions on the Visual Studio Marketplace after finding that the obfuscated code they contained wasn’t actually malicious. The two VSCode extensions, which count over 9 million installs, were pulled from the VSCode Marketplace in late February over security risks, and their […]
CISOs, are your medical devices secure? Attackers are watching closely
The adoption of connected medical devices, collectively called the Internet of Medical Things (IoMT), has transformed patient care. However, this technological advancement has also introduced cybersecurity challenges to safeguard patient safety and uphold organizational security. Securing IoMT: Prioritizing risks IoMT devices, ranging from infusion pumps to imaging systems, are often interconnected and communicate over networks, […]
X suffered a DDoS attack. Its CEO and security researchers can’t agree on who did it.
Social media service X was hit by a series of distributed denial-of-service attacks Monday, which rendered the platform formerly known as Twitter inaccessible at times for users with intermittent outages and errors, according to researchers. The cause of those attacks has been much harder to discern. Elon Musk, the site’s owner, described the incident as […]
Cisco ClamAV anti-malware scanner vulnerable to serious security flaw
Patch released for bug that poses a critical risk to vulnerable technologies A security flaw in a bundle anti-malware scanner product has created a serious security risk for some products from networking giant Cisco. More particularly, a vulnerability in the ClamAV scanning library (tracked as CVE-2023-20032) created a critical security risk for Cisco’s Secure Web […]
OBSCURE#BAT Malware Uses Fake CAPTCHA Pages to Deploy Rootkit r77 and Evade Detection
Mar 14, 2025Ravie LakshmananThreat Intelligence / Malware A new malware campaign has been observed leveraging social engineering tactics to deliver an open-source rootkit called r77. The activity, condemned OBSCURE#BAT by Securonix, enables threat actors to establish persistence and evade detection on compromised systems. It’s currently not known who is behind the campaign. The rootkit “has […]