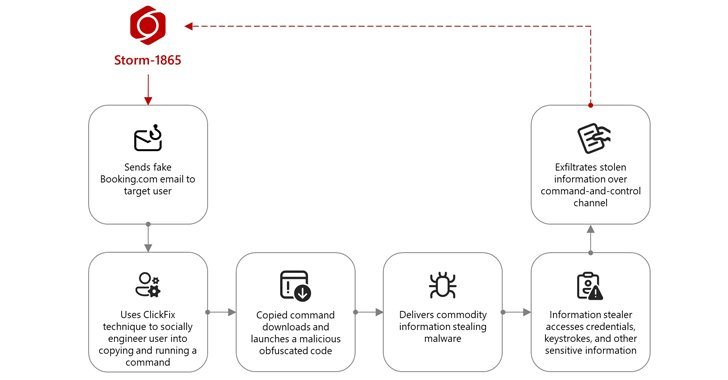
Microsoft has shed light on an ongoing phishing campaign that targeted the hospitality sector by impersonating online travel agency Booking.com using an increasingly popular social engineering technique called ClickFix to deliver credential-stealing malware. The activity, the tech giant’s threat intelligence team said, started in December 2024 and operates with the end goal of conducting financial […]
Category: Uncategorized
Trade groups worry information sharing will worsen without critical infrastructure panel, CISA law renewal
Business groups told lawmakers Tuesday that they fear cyber threat information sharing could drop off in light of the Trump administration’s move to eliminate a critical infrastructure committee and given the pending expiration of a 2015 law. The Critical Infrastructure Partnership Advisory Council (CIPAC) fell among a swath of government advisory committees that Homeland Security […]
CVSS system criticized for failure to address real-world impact
JFrog argues vulnerability risk metrics need complete revamp ANALYSIS Weaknesses in the existing CVSS scoring system have been highlighted through new research, with existing metrics deemed responsible for “overhyping” some vulnerabilities. So-called “overinflated” ratings are potentially eating up the limited time of cybersecurity teams who may then not be focused on the bugs most likely […]
The best free VPNs of 2025: Expert tested
Virtual private network (VPN) services cost money to run, so you should always approach supposedly “free” services with caution. “Free” in the VPN world usually means that providers will give you a connection but make money from you in other ways. They may hide crucial features behind a paywall, display ads, or worse — they […]
1 Million Third-Party Android Devices Have a Secret Backdoor for Scammers
Researchers from multiple firms say that the campaign seems to come from a loosely connected ecosystem of fraud groups rather than one single actor. Each group has its own versions of the Badbox 2.0 backdoor and malware modules and distributes the software in a variety of ways. In some cases, malicious apps come preinstalled on […]
Trump nominates cyber vet Sean Plankey for CISA chief amid DOGE cuts and firings
Mark Montgomery, former executive director of the Cyberspace Solarium Commission and now a cybersecurity leader at the Foundation for Defense of Democracies, tells CSO that Plankey is a “great hire” and “is just what CISA will need as we defend against an increasingly aggressive nation-state adversary in China.” Former Obama administration cybersecurity official Ari Schwartz, […]
Best 8 Endpoint Protection Software in 2025
Endpoint protection software works like a security system for a digital hotel. They equip each ‘room’ – in our case work device – with a lock, alarms, video surveillance, etc. This way they make sure each visitor or hotel employee uses the private or common spaces safely and legit. Endpoint protection tools act like digital […]
Unmasking a Global Threat in 2024
“Crazy Evil” Cryptoscam Gang Since 2021, the “Crazy Evil” cryptoscam gang has escalated into one of the most prolific cybercriminal groups targeting digital assets. Specializing in identity fraud, cryptocurrency theft, and information-stealing malware, Crazy Evil employs a well-coordinated network of traffers — social engineering experts tasked with redirecting legitimate traffic to malicious phishing pages. Crazy […]
Chinese State-Sponsored RedDelta Targeted Taiwan, Mongolia, and Southeast Asia with Adapted PlugX Infection Chain
Summary: Between July 2023 and December 2024, Insikt Group observed the Chinese state-sponsored group RedDelta targeting Mongolia, Taiwan, Myanmar, Vietnam, and Cambodia with an adapted infection chain to distribute its customized PlugX backdoor. The group used lure documents themed around the 2024 Taiwanese presidential candidate Terry Gou, the Vietnamese National Holiday, flood protection in Mongolia, […]
How Some State Health Privacy Laws Throw a Curveball at AI
Some state privacy laws, such as Washington State’s My Health My Data Act, could throw a curve ball in the use of certain consumer information for artificial intelligence and machine learning endeavors, said regulatory attorney Adam Greene of the law firm Davis Wright Tremaine. “If you’ve got consumer health data that falls outside of HIPAA, […]