Meta warns of actively exploited flaw in FreeType library Pierluigi Paganini March 13, 2025 Meta warned that a vulnerability, tracked as CVE-2025-27363, impacting the FreeType library may have been exploited in the wild. Meta warned that an out-of-bounds write flaw, tracked as CVE-2025-27363 (CVSS score of 8.1), in the FreeType library may have been actively exploited in attacks. “An […]
Category: Uncategorized
GitGuardian Report: 70% of Leaked Secrets Remain Active for Two Years, Urging Immediate Remediation
Boston, USA, March 11th, 2025, CyberNewsWire GitGuardian, the security leader behind GitHub’s most installed application, today released its comprehensive “2025 State of Secrets Sprawl Report,” revealing a widespread and persistent security crisis that threatens organizations of all sizes. The report exposes a 25% increase in leaked secrets year-over-year, with 23.8 million new credentials detected on […]
5 Best NIS2 Compliance Software and Solution Providers
The European Union’s Network and Information Systems Directive 2 (NIS2) is now in effect. And, throughout 2025, governments across the continent will be transposing it into national law. Complying with the regulation involves a combination of changes to workflows, employee behavior, and technology. There isn’t a single ‘turnkey’ solution that will make you compliant on […]
Russian Influence Operations Targeting Germany’s 2025 Elections
Executive Summary The German federal elections, scheduled for February 23, 2025, are the target of malign influence operations linked to Russia and Russia-based actors. As of mid-February 2025, Insikt Group assesses that, despite their persistence, these efforts have very likely not meaningfully altered voter behavior or shaped public opinion in a manner advantageous to Russia’s […]
Russian Influence Operations Targeting Germany’s 2025 Elections
Executive Summary The German federal elections, scheduled for February 23, 2025, are the target of malign influence operations linked to Russia and Russia-based actors. As of mid-February 2025, Insikt Group assesses that, despite their persistence, these efforts have very likely not meaningfully altered voter behavior or shaped public opinion in a manner advantageous to Russia’s […]
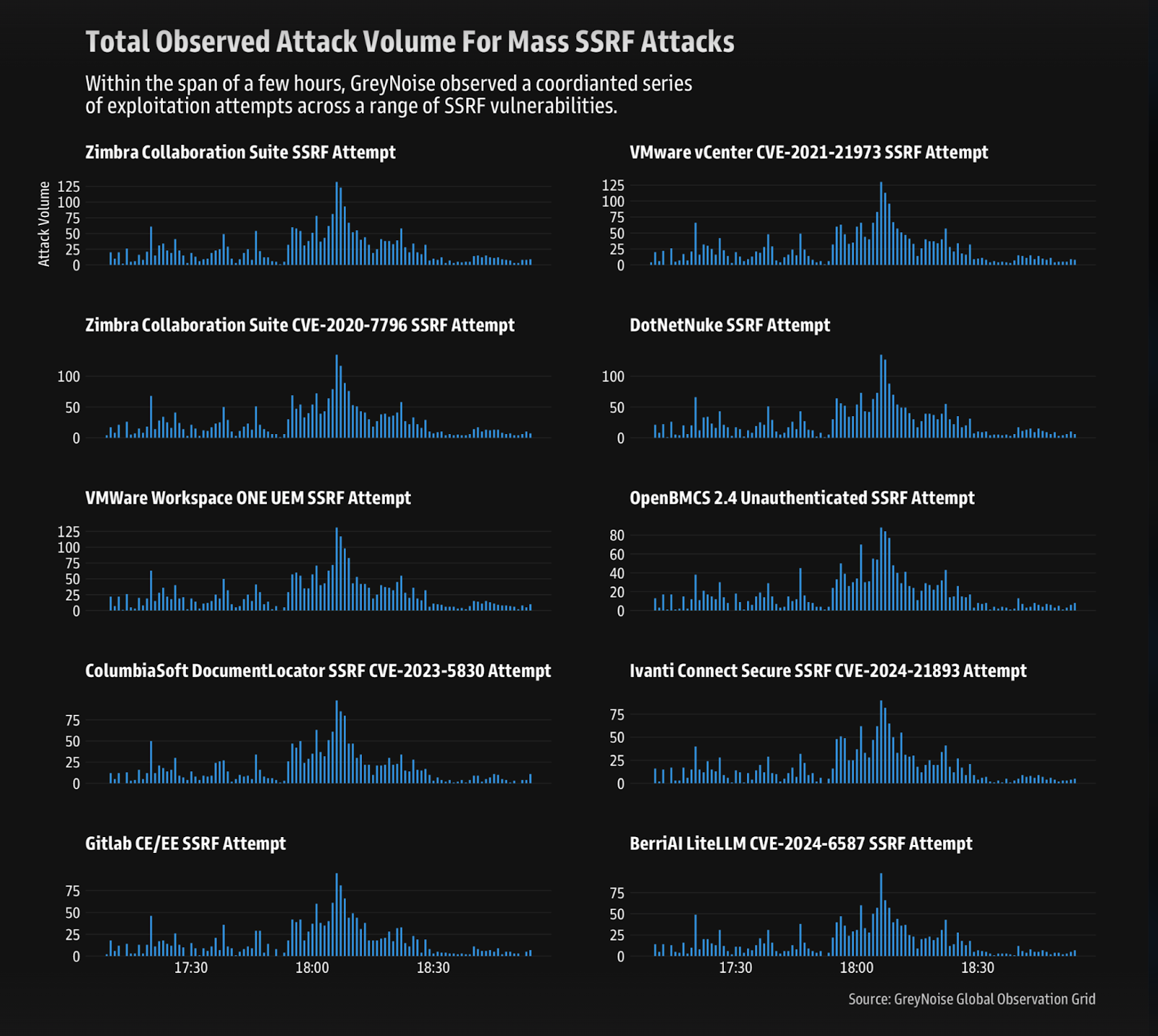
Experts warn of a coordinated surge in the exploitation attempts of SSRF vulnerabilities
Experts warn of a coordinated surge in the exploitation attempts of SSRF vulnerabilities Pierluigi Paganini March 13, 2025 Researchers warn of a “coordinated surge” in the exploitation attempts of SSRF vulnerabilities in multiple platforms. Threat intelligence firm GreyNoise observed Grafana path traversal exploitation attempts before the Server-Side Request Forgery (SSRF) surge on March 9, suggesting […]
FBI and CISA Urge Enabling 2FA to Counter Medusa Ransomware
FBI and CISA warn of Medusa ransomware attacks impacting critical infrastructure. Learn about Medusa’s tactics, prevention tips, and why paying ransoms is discouraged. A joint advisory by the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) has revealed a particularly aggressive digital threat- a criminal operation, known as the Medusa […]
Can AIs be psychopaths, and why we should be AI optimists • Graham Cluley
In episode 41 of the AI Fix, our hosts learn that society needs to be completely reordered by December, Grok accuses Trump of being a Russian asset, Graham discovers that parents were wrong about computer games all along, and Mark wonders if a kung-fu kicking robot from Unitree is the hero that we need. Graham […]
Ransomware gang creates tool to automate VPN brute-force attacks
The Black Basta ransomware operation created an automated brute-forcing framework dubbed ‘BRUTED’ to breach edge networking devices like firewalls and VPNs. The framework has enabled BlackBasta to streamline initial network access and scale ransomware attacks on vulnerable internet-exposed endpoints. The discovery of BRUTED comes from EclecticIQ researcher Arda Büyükkaya following an in-depth examination of the […]
94% of Wi-Fi networks lack protection against deauthentication attacks
A recent report from Nozomi Networks Labs, based on an analysis of over 500,000 wireless networks worldwide, reveals that only 6% are adequately protected against wireless deauthentication attacks. Most wireless networks, including those in mission-critical environments, remain highly exposed to these attacks. In healthcare, for example, vulnerabilities in wireless networks could lead to unauthorized access […]